Millions of malicious bots scan WordPress sites for weak usernames and passwords to reveal vulnerabilities. If you’re certain your website is secure, fine, but just to be safe, you should probably read this post.
As great as WordPress is, there are a few things about it that seriously annoy me. While the razzmatazz of this CMS is impressive, you might be failing to notice some basic security settings that could make the difference between being hacked and being left alone.
Make no mistake – hackers will target ANY WordPress blog because the attempts are often made by automatic sub routines scouring the web daily for vulnerabilities.
These are called brute force attacks and that’s what I want to draw your attention to right now.
A tutorial video is included at the end.
WordPress Username Vulnerabilities
I’m guessing you have already changed your WordPress username from the default “admin” to something hard to guess?
Good, that’s a start.
But if I had a penny for every time a WordPress website owner didn’t change their user_nicename in phpMyAdmin I’d have enough to buy a good steak dinner.
It may be you’ve never even heard of user_nicename. That’s okay. Some of the top bloggers don’t even know about this.
Everything will become clear after I explain what this has to do with website security and how it concerns your URL.
WordPress User Security
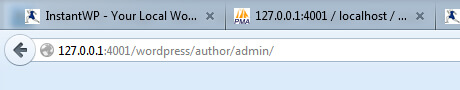
Look at the screenshot below. What do you see in the last part of the URL?
In case the image hasn’t loaded, here’s a reiteration below:
/author/admin/
That, my friend, is your WordPress username.
Even if you change it to something other than “admin” it will still show up in the author archive URL.
It’s a dead give away. Go to any WordPress site, and look for the Posted by section under the title of a post.
Unless the webmaster has already configured the database to show something different, you’ll be able to find out what that webmaster’s logging in name is!
It’s crazy!
This is a general WordPress problem that CAN be corrected in phpMyAdmin.
If you don’t take steps to resolve this now, you are leaving yourself wide open to potential attack.
Think about it: you’re giving potential hackers part of what they need to begin a brute force automatic hacking campaign to try and access your site!
Once they have your username, they just need your password (and most people use a weak password.)
You might get away with it, but is it worth waiting to find out?
The Fix: A Simple phpMyAdmin Tweak
If you follow the instructions I’m about to give you, it is possible to disguise your username by altering how the author URL/slug appears, thus hiding the real username you use to log in.
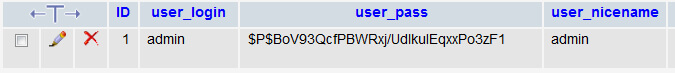
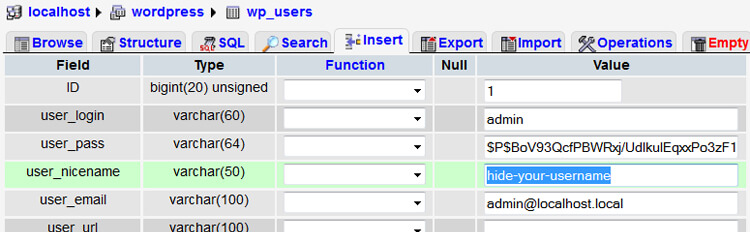
The screenshot below is from phpMyAdmin.
Notice how the user_nicename is identical to the user_login.
It uses “admin” in both instances.
This is our problem. You MUST change the user_nicename to something different.
It doesn’t alter your logging in credentials. It just hides your username from prying eyes.
You need to access the table wp_users in your main database inside phpMyAdmin.
If you use cPanel for hosting, you’ll find the phpMyAdmin icon under the databases section.
In the example, the database is called “wordpress”. Your database might be called something different.
Access the correct database and click wp_users.
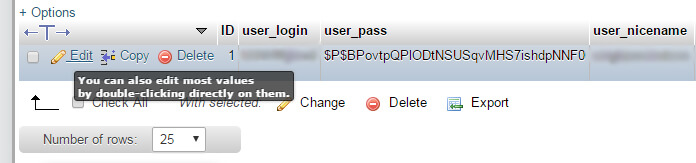
Next, you’ll be presented with a row inside this table that you can edit by clicking the pencil icon in the screenshot below.
Then you can change the setting from “admin” (or whatever is showing up in the author archive URL) to something else.
I’ve replaced the defaults with the hyphenated example shown below. I’ve used small-biz-geek for my own website.
Your version of phpMyAdmin might be a little different depending on your host. Another way to edit the wp_users table is to click the “browse” icon shown in the screenshot below.
Click the icon and you can access and edit the rows containing the user_nicename.
While you can make this tweak on the live version of your website database, I highly recommend doing it while you’re in the offline/development phase – the localhost if you’re using WAMP.
InstantWP is another piece of software for simulating a localhost for WordPress and you can access the same if not very similar database settings from there.
Eventually, you want something that looks a bit like the screenshot below:
(Never use admin as your user_login. The example shown is hypothetical.)
I’ve produced a short video showing you how to solve the issue if my instructions are not clear:
Free WordPress Security Plugin
It is probably worth your while using the WordFence Security plugin for WordPress since this monitors all login attempts. many of these attempts will be the brute force hacker bots looking for weaknesses.
WordFence send you an email digest to let you know which usernames were used as part of a login attempt.
If you run a multi author blog, this is useful because it actually shows both authorised and unauthorised logins. If a fellow team member logs in, you’ll get an email letting you know.
🏗️ Dodge WordPress Website Disasters: Use a Localhost for Development
🤔 Can We Really Trust WordPress Plugins? Back Up Your Site Manually NOW
🙈 This WordPress Media Uploader Problem Makes Your Blog Look Amateur



Thankyou for posting this, it never even occurred to me someone might be able to get my username this way. I hav heard of the brute force attempts but always assumed they go for bigger sites?
The brute force bots will have at it with any WordPress website. Out of the box, WP is just not secure.
You do *NOT* need to use phpMyAdmin to change your user nicename. User nicename can be set per user, using a combination of the “Nickname” and “Display name publicly as” field on the user profile editor.
To be honest. Don’t install phpMyAdmin at all…
Personally I use a different name/username combo, and my Login is restricted to known IP’s using Htaccess. So even I can only login to my WP Admin from “known” locations.
The majority of break ins are via shoddy plugins, or other vectors like phpMyAdmin or more recently the Operating system itself. Brute force whilst needing to be aware of, most attackers don’t even bother scanning for the username and just hammer admin regardless, in my experience
Hi Barry, thanks for you thoughts. I’m not sure we’re referring to the same thing here… user_nicename is revealed in the author archive URL when you click the publicly displayed name.
Indeed to correct. user_namename is the URL safe version of display_name which is automatically generated from the dropdown selector for “Display publicly as”.
I’d still not install phpMyAdmin for this.
And a better solution over all. For a single user site is to throw in a plugin or theme patch for disabling the /author/ section of the site, and remove the Author links altogether from your theme, since the author section would just be duplicating the home page content/main archive.
Now I have gone and checked the source and tested, and I stand corrected. You can’t change the user_nicename easily from the backend. So my apologies. I was outraged at the suggestion of using phpMyAdmin to fix this when there are better ways. Installing phpMyAdmin is not one of them
Yes I do disable the Author name on some sites. The plugin Genesis Simple Edits can be used to edit out that info.
Thanks, great tip, I wasn’t even aware of this.
I agree that there are easier ways to hack a site than using brute force, but this fix is so simple, why not making it harder for those who will try brute force 🙂
I have two users on my website. I changed user_nicename step-by-step as menioned above for both users. Admin’s nice name is changed, but the other user now shows admin as nice name in links, but in phpmyadmin both are different.
Did I missed something???
Can you email me with more details? I’m curious to know what has happened here but I appreciate you can’t disclose too much here in the public comments.
It might have something to do with User Profile settings in your WordPress dashboard. There’s a difference between the username anchor text and the URL, which I’m sure you’re aware of already.
Perhaps you can send me a screenshot to my email. You can blur out any information you don’t want me to see if you’re screen capping phpMyAdmin tables.
Thanks for your help, sir. My website is working fine now.