In 2016, cyber criminals profited $450 billion. With dedicated, professional criminal organisations operating with impunity, the least you can do is review your password strength.
These days our entire lives seem to be guarded by passwords. Sadly, the ability to lie, manipulate, misinform and mislead is becoming more sophisticated as thieves learn to slip in and out of your online accounts undetected. 🔓
You’ve probably received text messages, emails and phone calls from someone claiming to be from a real organisation, whether it’s your bank, Microsoft, HMRC, eBay, PayPal, Royal Mail or any other well-known name. I had a WhatsApp message that turned out to be a Hays Recruitment scam. 🥸
I received a text alerting me of suspicious activity on my bank account and went to great lengths to discover the legitimacy of this message. Turns out it was real, but better safe than sorry, was my reasoning. 👀😓
What cybercriminals want to is to break the authentification mechanism, and passwords are part of the entirety of that mechanism. 🧨
Even if you don’t have your bank account emptied, you could still be a victim. Someone obtaining and selling your details in order to commit fraud against larger businesses makes you their proxy. ♟️
How Hackers Obtain Your Password
There three primary ways to get your password. Phishing, guessing and brute force.
Phishing 🎣
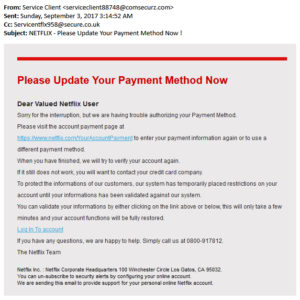
The first method is to trick you into giving it up willingly by sending you a scam email which directs you to a fake site where it can be stolen. This falls under the remit of human error because the user becomes unknowingly complicit in a socially-engineered attack.
This carrot and stick approach is not particularly sophisticated but people do fall for it. Receiving a fake email from a bank, PayPal, HMRC, utilities and entertainment providers is not uncommon.
You can normally spot fake emails by checking the email reply-to address, or by hovering your mouse cursor over the website address in the email body and looking at the preview on the bottom left.
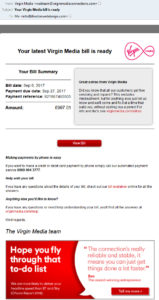
As I was writing this post an email came from Virgin Media, telling me that a bill was ready for me to pay. This came through to an email address I had never disclosed to them so I was suspicious. 🕵️
The email was convincing in that it cited and linked through to some legitimate pages on the VM website, but the reply to address was webteam@virginmediaconnections.com. 😒
They’d never used an email like that before, so I checked out www.virginmediaconnections.com and was faced with a parked domain. An inactive website.
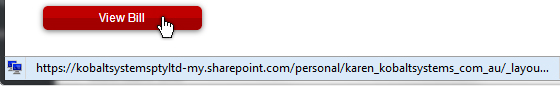
Furthermore, the “View Bill” button in the email linked to a completely different website. I didn’t click anything – obviously – but by hovering my cursor over the button, the preview URL in the bottom left corner was revealed. 🔍🦅😒
That was the trap, sprung and ready to decapitate. 🪤🔪
I sent the screenshot of the email to Virgin Media via their Twitter profile.
Guessing 🤔
Hackers use other information available online about you to guess the password. Many people use derivatives of names, dates, pets, significant places and locations.
They could be using digital spying techniques to gather information about you to join the dots.
If you’re the kind of person who uses the same passwords for different services, it’s going to be easier to hack you. Facebook’s own Mark Zuckerberg fell victim to this.
Brute Forced Entry 🔨
Brute force is where a hacker basically just tries every possible password until they get the right one.
It’s always possible to brute force a system if you have enough computers to do it – like a government.
Using brute force, hackers can cycle through 8 billion password combinations per second. Research from a Norwegian security convention in 2013 claimed that an 8 character password could be cracked in 6 hours.
The longer the password, the longer it takes to crack. A very complex password could take up to ten years to crack.
It’s possible to theoretically calculate the time it would take to crack any password, but how accurate these estimates are is up for debate.
Choosing a Strong Password
Many websites and online services are beginning to reject weak passwords at the sign up stage. ❌
A good password should contain:
✅ UPPERCASE letters (ABC)
✅ Lowercase letters (abc)
✅ Numbers (123)
✅ Spaces ( )
✅ Punctuation (.,:;-!?)
✅ Symbols (@&+=>$#*^~)
✅ Respelling (i.e., no words that can be found in a dictionary: for example, using “kwean”, instead of “queen”)
✅ More than 15 characters
Generating a Complex Password
I use a password generator to come up with strong, complex passwords. These are not supposed to be easy to remember, so write it down somewhere. ✍️📃📎
When you write passwords down by hand, be mindful of subtle differences between things like the letter “o” and the number “0”. 🧐
Choosing A Memorable Password
If you need to be able to remember your password, you can use three random words: something you know, something you have, something you are.
The UK Government are running TV ads encouraging the use of stronger passwords comprising of three random words.
Banks are beginning to run media campaigns across TV and the internet encouraging this too:
Don't let criminals steal your information. For more advice visit Lloyds Bank: https://t.co/9GFyoHRhtN @TakeFive pic.twitter.com/NiIwUw5AfW
— Lloyds Bank (@LloydsBank) May 30, 2017
Send Passwords Safely
I’ve worked with clients who have sent me passwords and usernames together as plain text in an email message. Not good. 🚩
Personal data in emails can be intercepted easily. 🥷
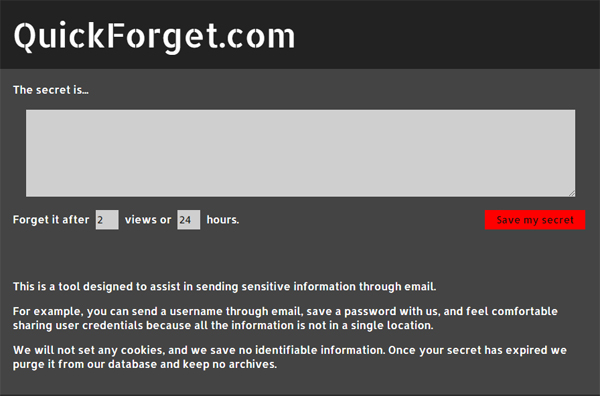
Instead, try the free QuickForget by Automattic. Paste a password into the form and set it to be forgotten after so many views or so many minutes.
Share the unique link that is generated with your recipient and the data will be destroyed after the link expires. 🤓👍
Store Passwords Safely
You need to guarantee the physical security of written or recorded passwords. Online password storage services like LastPass (not an affiliate link) are available as a freemium service, but it depends on how much you trust them not to get hacked. And LastPass was hacked, although the user data was not compromised.
A frequently backed up and carefully guarded password protected word document containing your data in plain text on a USB drive is an option. A locked drawer or safe helps. 🗄️
I’ve put together an MS Word document to store website credentials. It’s convenient but poses a risk; all the details are lumped together but you can store this offline and in a safe place. 📄
Disposing of Data
If you need to dispose of passwords printed or written on paper, use a decent shredder. The importance of destroying data correctly cannot be emphasised enough. 💾✂️
Don’t overlook the digital storage methods either. Disk data can be easily recovered after it’s been deleted, and I know because I’ve recovered long lost files using data recovery software I purchased for £60.
The Dark Web is Coming for You
You’ve heard of the dark web – the anonymous, unregulated underbelly of the internet – the place where anyone from arms dealers to perverts communicate away from the mainstream cyberspace. ⚠️
Here, hackers peddle their attack software and share information with one another on attack techniques. You can buy everything from a base-level attack to a more advanced version. 💣
You’ll see hacking products marketed in bronze, silver and gold levels, making data attacks routine, efficient and professional. 🥇🥈🥉
Be Ready to Prevent Hackers
Are you taking the issue as seriously as the bad guys are? 🔫
Keep in mind, that in most cyber attacks, people are the weak link. Break the person first, and the authentication system is more likely to break.
On a side note, some of the most successful scams (like MLM pyramid schemes) are not at all technically sophisticated.
As Caleb Barlow says in his TED Talk, we should be on a computer war footing. Improve your passwords, develop safer habits and review how and where your data is stored. 🚨
More on Information Security
🔒 Google Security Smackdown: Websites Without HTTPS Will Suffer
☠️ Privacy and Data Protection is a Matter of Life and Death
🕵️ Theresa May’s Snoopers’ Charter Gives Unprecedented Legal Surveillance Power to Spooks


I typically suggest to my users that they create their own algorithm to end up with a unique password for each website. I have also started to encourage the use of password managers such as 1-Password. What do you think of these practices?